We take care of vulnerabilities
before they cause damage.
Your business is only as strong as the foundations on which it is built. But how safe actually are these foundations? Even small vulnerabilities in your network can have a big impact.
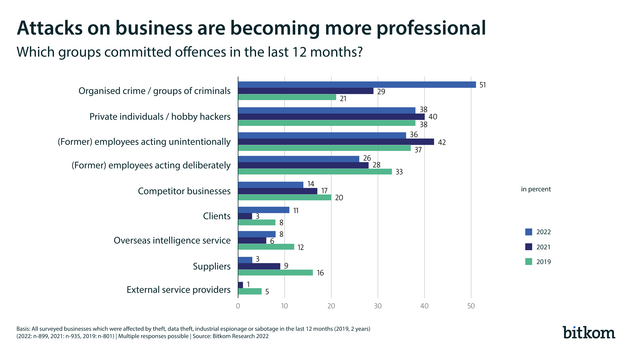
Sudden failure, data leaks or inefficient systems don’t just disrupt operations; they can also have expensive consequences. According to a Bitkom study, in 2022, German companies suffered 203 billion euro worth of damage as a result of cyber attacks.
What we can do for you
and what you don’t need to worry about any more.
Network
as a Service
- tenzing IT Ops bears the procurement costs and leases the hardware – OPEX.*
- Continuous support from tenzing IT Ops.
- tenzing IT Ops minimises the risk of failure through proactive monitoring.
- tenzing IT Ops takes responsibility for managing the network.
- tenzing IT Ops implements security measures.
- tenzing IT Ops scales the network in good time and with flexibility based on the progressing needs.
- Reduction of operating costs thanks to an efficient use of resources. (Hardware, energy and FTE for your IT professionals)
- tenzing IT Ops provides the hardware.
*We purchase the property at the client network, whether already existing (sale & lease) or new.
Managed
Network
- Client pays for the hardware – CAPEX.
- Continuous support from tenzing IT Ops.
- tenzing IT Ops minimises the risk of failure through proactive monitoring.
- tenzing IT Ops takes some of the responsibility for network management.
- tenzing IT Ops implements security measures, to the extent that the hardware configuration permits this.
- tenzing IT Ops scales the network based on the progressing needs and availability.
- Reduction of operating costs thanks to an efficient use of resources. (Energy and limited FTE for your IT professionals)
- tenzing IT Ops provides the hardware.
Network
Support
- Client pays for the hardware – CAPEX.
- Client contacts tenzing IT Ops only in support cases.
- tenzing IT Ops minimises the risk of failure through automated monitoring.
- tenzing IT Ops takes responsibility for managing the network.
- tenzing IT Ops implements security measures.
- tenzing IT Ops scales the network in good time and with flexibility based on the progressing needs.
- Reduction of operating costs thanks to an efficient use of resources. (Hardware, energy and FTE for your IT professionals)
- tenzing IT Ops provides the hardware.
Advantages in detail
You get
a trustworthy partner.
You decide
which resources we take on for you.

A fixed point of contact who knows you and makes sure that we can respond quickly and flexibly to changes within your organisation at any time is always part of the package – regardless of the size of your business or your location in Europe.
Our services are based on defined SLAs and guarantee you the highest degree of security in budget planning and your IT functionality.
Everything was working fine before. Somehow.
You decide which financial and personnel resources you would like to replace or supplement with our services. Simply decide on the financing model that supports your business the best: CAPEX, OPEX or a mixed form.

Keep an overview
thanks to the monthly network analyses.
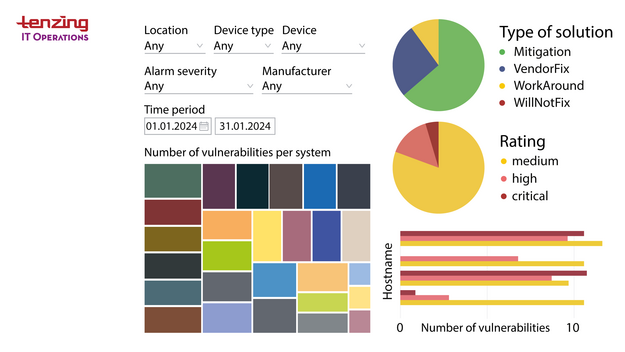
Is your network doing what it’s supposed to?
Our monthly analyses provide:
Our monthly reports (IT Management Summary) are based on real-time monitoring of all network activities. We follow all performance indicators so that we can identify bottlenecks at an early stage as well as long-term trends. Our monitoring allows us to identify, isolate and rectify vulnerabilities quickly. Our extensive analysis tools form an excellent basis to make well-grounded decisions, also with regard to budget planning. These tools enable us to interpret, categorise and prioritise errors. Data protection is, of course, always guaranteed.
Our start routine forms the basis
of good cooperation.

Non-binding initial discussion with indication of costs available straight away

Initial infrastructure analysis to record and evaluate your IT environment

Optional validation (PoC) during a parallel operation for test purposes

Recommendations for action and quotes for taking measures

Permanent reporting ensures that you keep an overview of operations at all times.
Request a
non-binding quote today
Whether you call or send an email, we’ll be delighted to hear from you. You will be surprised how quickly we can prepare a quote to give you an initial guideline value.

Sales Manager
We are tenzing IT Ops,
the network experts from Lübeck.

The tenzing IT system house is situated in charming northern Germany, in Lübeck to be precise. What part of the world could be better? For over 30 years, we have focused on the areas network, IT security and data centres. And it’s definitely worthwhile.
We know these topics better than practically anyone else. This is highlighted by our trust-based cooperation with known manufacturers such as Hewlett Packard Enterprise/Aruba. Many notable clients value our expertise, within Germany and also beyond.
In addition to numerous medium-sized businesses in the region, our clientele also includes various public authorities and international groups who value our personal and efficient cooperation. We are proud of that fact that our founders and owners Björn Meyer and Gunnar Petersen play an active role in the business and allow their far-reaching expertise to influence projects.
Over the years, they have developed an extensive portfolio of services surrounding the three areas of business. In this way, tenzing doesn’t just impress when it comes to active and passive components for network infrastructure; but also in areas such as cabling, server room retrofitting or radio relay solutions.
Our IT security makes sure that all systems within your business and the data stored within them are reliably protected from misuse, disclosure and theft. Complex data management with sophisticated server and storage concepts round off our portfolio.
Made just for you:
tailored managed services
In all three areas, managed service solutions play a key role. These are tailored to suit the relevant IT tasks of each individual business. Our managed service concepts are just as varied as the businesses that we support. They range from advisory support of existing IT departments in specific issues to complete insourcing of an IT department.
The entire IT market is moving ever faster to “as a Service” models. In order to react swiftly to market developments, we are also taking this step and grouping together corresponding offers at tenzing IT Operations GmbH.
tenzing would like to continue to support clients in the future in a way that you would expect from a business named after the most famous Sherpa*: calmly and reliably. So you don’t need to think about your IT any more – we’ll do that for you.
* Tenzing Norgay helped Sir Edmund Hillary achieve his greatest success in being the first to reach the summit of Mount Everest, while remaining in the background himself.
Frequently asked
questions and answers
There are no investment costs for NaaS. You pay a fixed monthly service fee and thus optimise your budget planning.
No, our NaaS can of course be distributed over several locations – we also have international clients which we support in their operations throughout Europe.
Yes. Our team of IT specialists can take on the complete operation and support of the provided network while you are kept informed of all key occurrences and can focus on your core business.
The term of contracts can be defined on a case-by-case basis. Most clients start with a minimum of 36 months.
There are no specific requirements. Our experts can advise you in advance with regard to your individual needs so that we can prepare a tailored solution out of the required hardware, software, and services.
Yes. If your requirements change during the term of the contract, the scope of services can be adjusted flexibly.
With our 30 years of experience, we’re not merely here to show off an extensive portfolio of services; we can also talk about the numerous partners and clients who count on us and rely on our expertise. You too can become a satisfied customer.
We look after your network and guarantee that all components are taken into account. This also includes statutory requirements and regulations. This is why we deal with experts in this area on your behalf and expand our portfolio so that you can focus on your core topics.